Adaface Sample Questions
Adaface assessments are tailored to your job description by our subject matter experts from our library of 10000+ questions. We've made a small portion of our library public to demonstrate the quality of questions in our library. All questions used in Adaface assessments are non-googleable and designed to test for on-the-job skills.
Skills
Aptitude & Soft Skills
Product & Design
Visualization & BI Tools
Programming Languages
Frontend Development
Backend Development
Data Science & AI
Data Engineering & Databases
Cloud & DevOps
Testing & QA
Accounting & Finance
Microsoft & Power Platform
CRM & ERP Platforms
Cybersecurity & Networking
Marketing & Growth
Oracle Technologies
Other Tools & Technologies
| 🧐 Question | |||||
|---|---|---|---|---|---|
|
Medium
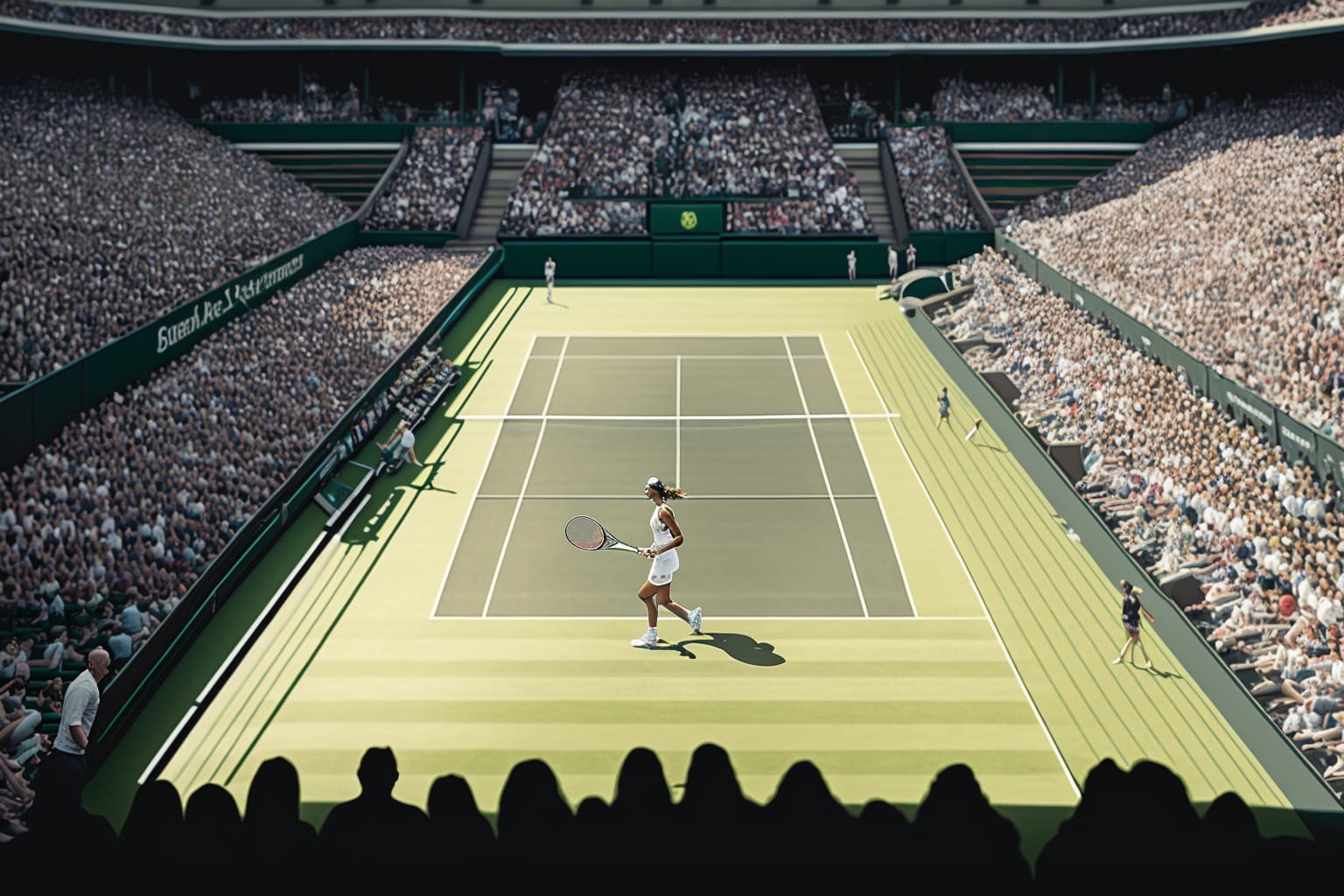
Tennis Players
|
Solve
|
||||
|
|
|||||
|
Medium
Code language
|
Solve
|
||||
|
|
|||||
|
Medium
Increasing monthly gross profit
|
Solve
|
||||
|
|
|||||
|
Medium
Claims for a new drug Xylanex
|
Solve
|
||||
|
|
|||||
|
Medium
China manufacturing
|
Solve
|
||||
|
|
|||||
|
Medium
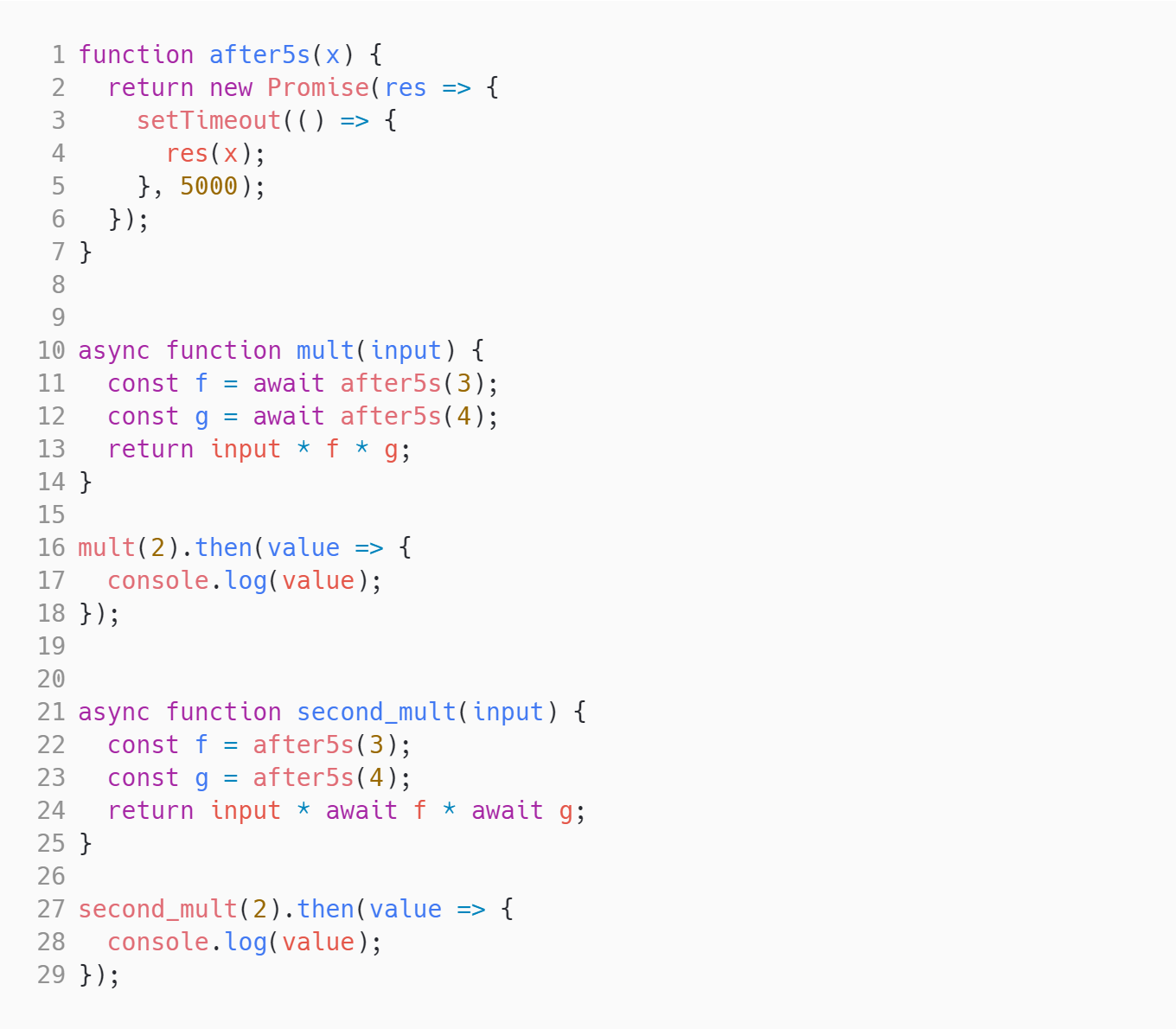
Async Await Promises
|
Solve
|
||||
|
|
|||||
|
Medium
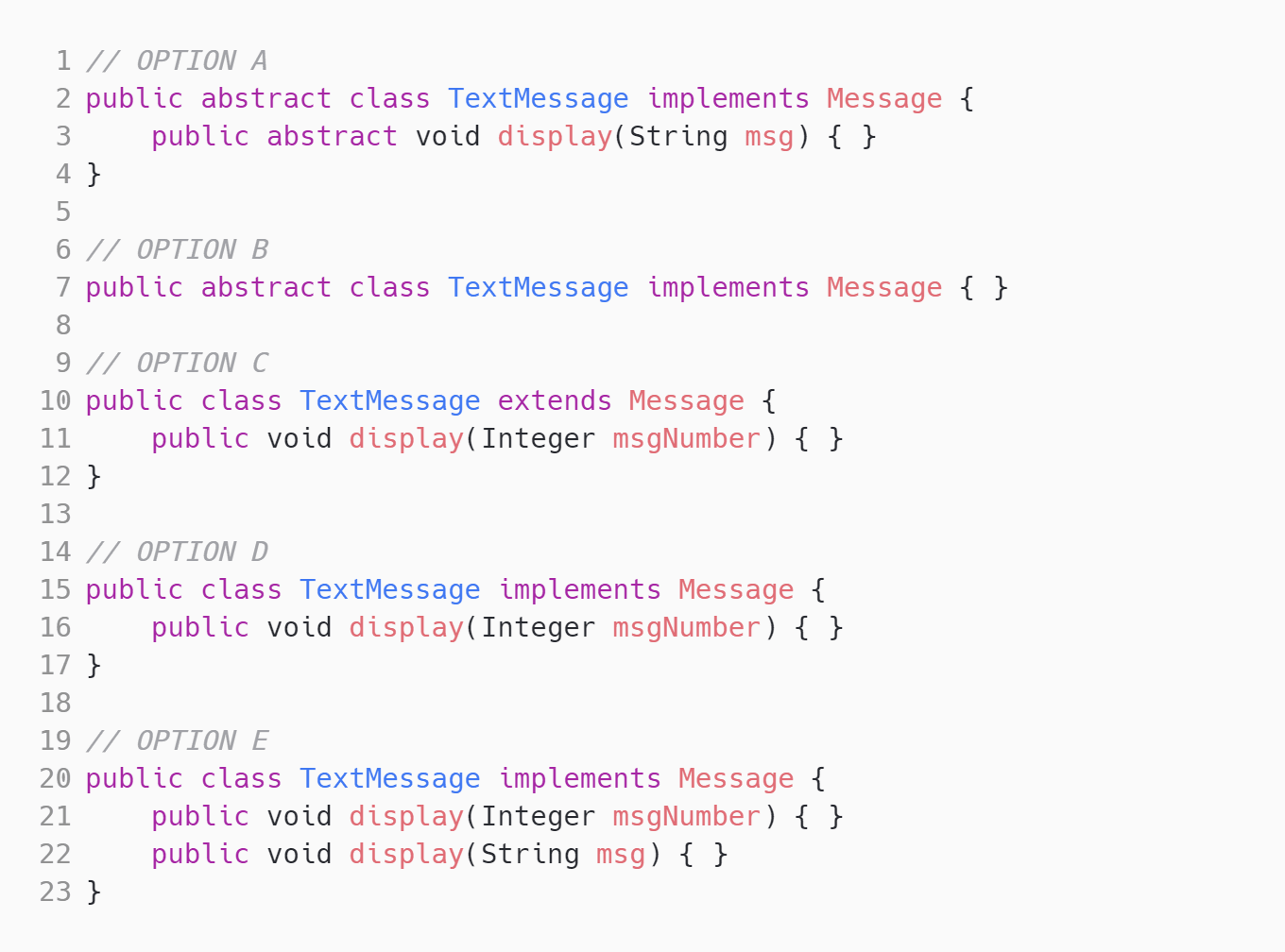
Abstract Interface
|
Solve
|
||||
|
|
|||||
|
Medium
Hooks with Conditional Rendering
|
Solve
|
||||
|
|
|||||
|
Medium
EC2DataProcessing
|
Solve
|
||||
|
|
|||||
|
Medium
Visitors Count
|
Solve | ||||
|
|
|||||
|
Medium
Data Filtering
|
Solve
|
||||
|
|
|||||
| 🧐 Question | 🔧 Skill | ||
|---|---|---|---|
|
Medium
Tennis Players
|
3 mins Logical Reasoning
|
Solve
|
|
|
Medium
Code language
|
2 mins Attention to Detail
|
Solve
|
|
|
Medium
Increasing monthly gross profit
|
2 mins Numerical Reasoning
|
Solve
|
|
|
Medium
Claims for a new drug Xylanex
|
2 mins Critical Thinking
|
Solve
|
|
|
Medium
China manufacturing
|
2 mins Verbal Reasoning
|
Solve
|
|
|
Medium
Async Await Promises
|
2 mins JavaScript
|
Solve
|
|
|
Medium
Abstract Interface
|
2 mins Java
|
Solve
|
|
|
Medium
Hooks with Conditional Rendering
|
3 mins React
|
Solve
|
|
|
Medium
EC2DataProcessing
|
2 mins AWS
|
Solve
|
|
|
Medium
Visitors Count
|
30 mins Coding
|
Solve | |
|
Medium
Data Filtering
|
2 mins Power BI
|
Solve
|
| 🧐 Question | 🔧 Skill | 💪 Difficulty | ⌛ Time | ||
|---|---|---|---|---|---|
|
Tennis Players
|
Logical Reasoning
|
Medium | 3 mins |
Solve
|
|
|
Code language
|
Attention to Detail
|
Medium | 2 mins |
Solve
|
|
|
Increasing monthly gross profit
|
Numerical Reasoning
|
Medium | 2 mins |
Solve
|
|
|
Claims for a new drug Xylanex
|
Critical Thinking
|
Medium | 2 mins |
Solve
|
|
|
China manufacturing
|
Verbal Reasoning
|
Medium | 2 mins |
Solve
|
|
|
Async Await Promises
|
JavaScript
|
Medium | 2 mins |
Solve
|
|
|
Abstract Interface
|
Java
|
Medium | 2 mins |
Solve
|
|
|
Hooks with Conditional Rendering
|
React
|
Medium | 3 mins |
Solve
|
|
|
EC2DataProcessing
|
AWS
|
Medium | 2 mins |
Solve
|
|
|
Visitors Count
|
Coding
|
Medium | 30 mins | Solve | |
|
Data Filtering
|
Power BI
|
Medium | 2 mins |
Solve
|

We evaluated several of their competitors and found Adaface to be the most compelling. Great library of questions that are designed to test for fit rather than memorization of algorithms.
Swayam Narain, CTO, Affable