Hiring the right Software Security Engineer is crucial for safeguarding your organization's digital assets and sensitive information. A well-crafted set of interview questions can help you identify candidates with the necessary skills, experience, and problem-solving abilities to excel in this critical role.
This blog post provides a comprehensive list of Software Security Engineer interview questions, categorized for different experience levels and specific areas of expertise. From basic concepts to advanced topics, these questions cover a wide range of security-related subjects, including threat modeling, vulnerability assessments, and situational scenarios.
By using these questions, you can effectively evaluate candidates' knowledge and practical skills in software security. Consider combining these interview questions with a pre-employment assessment to gain a more holistic view of candidates' capabilities and make informed hiring decisions.
Table of contents
10 Software Security Engineer interview questions to initiate the interview

To kickstart your interview process and gauge a candidate's foundational knowledge in software security, use these 10 essential questions. These queries are designed to assess basic understanding and spark discussions about key security concepts.
- Can you explain the concept of Defense in Depth and why it's important in software security?
- What's the difference between authentication and authorization in the context of application security?
- How would you go about securing API endpoints in a web application?
- What is Cross-Site Scripting (XSS) and how can it be prevented?
- Explain the principle of least privilege and how you would apply it in software development.
- What are some common methods for securely storing passwords in a database?
- How does HTTPS work and why is it crucial for web security?
- What is SQL injection and what measures can be taken to prevent it?
- Can you describe the OWASP Top 10 and why it's significant for software security?
- What's your approach to conducting a security code review?
9 Software Security Engineer interview questions and answers to evaluate junior engineers

To assess whether candidates possess the essential knowledge and problem-solving skills for a software security role, consider asking them these carefully crafted questions. Designed with junior engineers in mind, this list will help uncover their abilities to tackle real-world security challenges while keeping the interview engaging and insightful.
1. What steps would you take to respond to a data breach as a software security engineer?
In the event of a data breach, a typical response includes several key steps. First, it's crucial to contain the breach to prevent further damage, which involves identifying the affected systems and disconnecting them from the network.
Next, a thorough investigation should be conducted to understand the extent and impact of the breach. Gathering evidence and logs will help determine how the breach occurred and which data was compromised.
Strong candidates will articulate the importance of communicating with stakeholders, including customers and legal teams, and implementing measures to prevent future breaches. Look for candidates who emphasize timely and transparent communication, a methodical approach to investigation, and a commitment to continuous improvement.
2. How do you stay updated with the latest security threats and vulnerabilities?
Staying updated with the latest security threats and vulnerabilities is crucial for any security engineer. Candidates might mention subscribing to security newsletters, following industry blogs, and participating in online forums and communities.
Attending security conferences and workshops can also be a valuable way to learn about new threats and network with other professionals. Engaging with platforms like Twitter for real-time updates from security experts can also be helpful.
An ideal candidate will demonstrate a proactive approach to learning and staying informed, showing an eagerness to adapt to the ever-evolving nature of software security.
3. Can you describe a time when you identified a security risk in a project and how you addressed it?
In addressing this question, candidates should highlight a specific instance where they spotted a potential security risk, such as an insecure configuration or code vulnerability.
The candidate should describe the steps they took to communicate the risk to the relevant stakeholders and how they collaborated with the team to implement a solution. This could involve patching the vulnerability, updating software, or changing configurations.
Look for responses that not only focus on the technical solution but also emphasize communication, teamwork, and the ability to prioritize security in development processes. A strong candidate will link their actions to broader security practices, showing an understanding of how to hire software security engineers.
4. How would you explain the importance of software security to a non-technical stakeholder?
Explaining the importance of software security to non-technical stakeholders involves using relatable metaphors and avoiding jargon. One might compare software security to locking the doors and windows of a house to protect against intruders.
It's crucial to convey that software security is about safeguarding sensitive information and ensuring trust in digital products. Highlighting recent case studies of security breaches and their impacts can also be effective.
Seek candidates who can communicate complex ideas clearly and persuasively, demonstrating their ability to bridge the gap between technical and non-technical audiences. A good communicator will ensure all stakeholders understand the value and necessity of robust security measures.
5. How do you prioritize security tasks when faced with limited resources and time?
When resources and time are limited, prioritizing security tasks involves assessing the potential impact of each vulnerability. Candidates might use a risk assessment matrix, considering factors such as the likelihood of exploitation and the severity of the potential impact.
They should also discuss the importance of focusing on critical vulnerabilities that pose the highest risk and ensuring compliance with industry standards and regulations.
The ideal response will highlight the candidate's ability to balance short-term fixes with long-term solutions and their skill in making informed decisions under pressure. Attention to skills required for software security engineers could further demonstrate their preparedness for the role.
6. What role does encryption play in software security, and when would you use it?
Encryption is vital in software security as it protects data by converting it into a code, ensuring that only authorized parties can access it. It is used to secure data both in transit and at rest, making it unreadable without the correct decryption key.
Encryption is commonly used to protect sensitive information such as passwords, credit card numbers, and personal data. In addition, it plays a significant role in ensuring secure communications between systems and services.
Candidates should demonstrate a solid understanding of when and why to use encryption, emphasizing its importance in maintaining confidentiality and integrity. Look for those who can explain encryption concepts in simple terms, showing their ability to apply these principles effectively.
7. How would you handle a situation where a developer disagrees with a security recommendation you made?
In such a situation, open communication and collaboration are key. The candidate should discuss their approach to understanding the developer's perspective and clarifying the rationale behind their security recommendation.
They might talk about presenting evidence or data to support their position and being willing to find a compromise that addresses both security and development needs.
Evaluators should look for candidates who demonstrate empathy, negotiation skills, and the ability to maintain positive relationships while advocating for security best practices. A strong response will highlight the candidate's commitment to fostering a security-first culture within the development team.
8. What are some effective ways to raise security awareness within a development team?
Raising security awareness within a development team involves regular training and workshops to keep security top of mind. Candidates might suggest integrating security into the development lifecycle through practices like secure coding guidelines and regular security reviews.
Gamification, such as security challenges or capture-the-flag events, can make learning engaging and foster a culture of continuous improvement. Sharing success stories and lessons learned from past incidents can also be impactful.
Ideal candidates will emphasize the importance of making security a shared responsibility and demonstrate innovative approaches to keeping the team informed and motivated to prioritize security in their work.
9. How do you ensure compliance with industry security standards in your projects?
Ensuring compliance with industry security standards involves staying informed about relevant regulations and guidelines, such as GDPR or HIPAA, and integrating them into the development process. Candidates should discuss conducting regular audits and security assessments to identify gaps and address them proactively.
They might also mention implementing automated tools to monitor compliance and generate reports, ensuring that the project remains aligned with standards over time.
Strong candidates will demonstrate a proactive approach to compliance, emphasizing their ability to translate regulatory requirements into actionable security measures. They should showcase their understanding of the importance of staying up-to-date with evolving standards in the industry.
18 advanced Software Security Engineer interview questions to ask senior engineers

When interviewing senior Software Security Engineers, it's essential to delve deep into their expertise and experience. This list of advanced questions will help you gauge their technical skills and understanding of complex security concepts. Use them to identify candidates who can effectively safeguard your applications and data. For more insights, check out our Software Security Engineer job description.
- Can you explain how you would implement secure coding practices in a development team?
- What is your experience with threat modeling, and can you describe a situation where it was particularly beneficial?
- How do you handle security vulnerabilities discovered in third-party libraries or dependencies?
- What strategies would you use to ensure secure software development lifecycle (SDLC) practices are followed?
- Can you discuss the differences between static and dynamic analysis tools in security scanning?
- How would you approach training developers on secure coding techniques?
- What are the key considerations when performing a risk assessment for a new software project?
- Describe a situation where you had to balance security measures with product usability. How did you handle it?
- Can you explain the concept of secure software architecture and how it's applied in your projects?
- How do you evaluate the effectiveness of security controls implemented in a software system?
- What metrics do you consider important for measuring the security posture of a software project?
- Can you share your experience with incident response planning and how you would incorporate it into a software project?
- What role do you think automated security testing should play in the development process?
- How do you keep abreast of the evolving landscape of security threats and best practices?
- Can you discuss a specific security incident you managed and the lessons learned from it?
7 Software Security Engineer interview questions and answers related to threat modeling
To pinpoint the perfect candidate for a Software Security Engineer role, it’s crucial to evaluate their understanding of threat modeling. This set of questions is designed to help you uncover a candidate's ability to identify and mitigate potential threats, ensuring your software stays as snug as a bug in a rug. Use these questions during interviews to dive deep into their practical knowledge and strategic thinking.
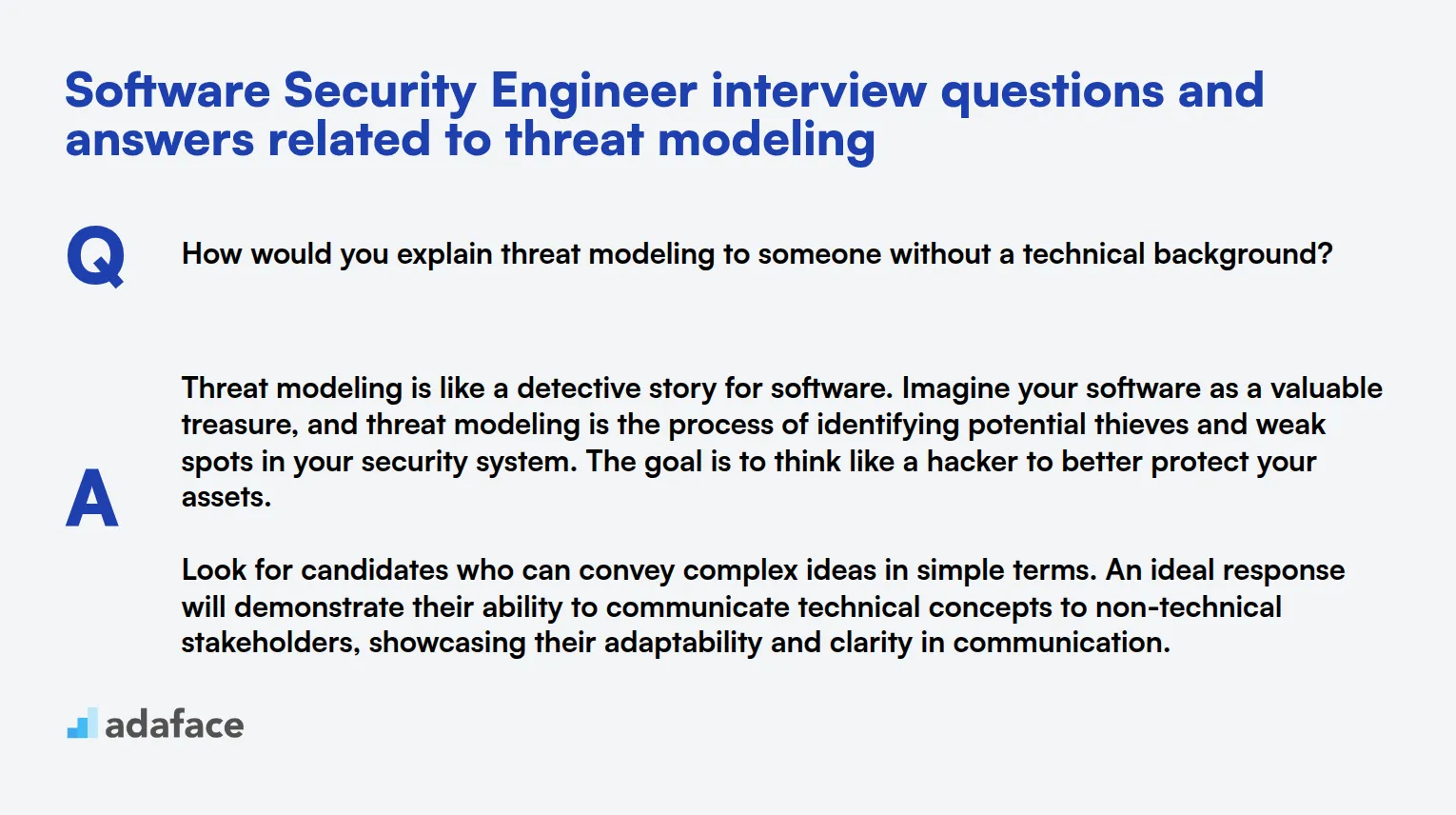
1. How would you explain threat modeling to someone without a technical background?
Threat modeling is like a detective story for software. Imagine your software as a valuable treasure, and threat modeling is the process of identifying potential thieves and weak spots in your security system. The goal is to think like a hacker to better protect your assets.
Look for candidates who can convey complex ideas in simple terms. An ideal response will demonstrate their ability to communicate technical concepts to non-technical stakeholders, showcasing their adaptability and clarity in communication.
2. What are the key steps you would take to perform threat modeling on a new application?
To perform threat modeling, one would typically start by understanding the application and its architecture. Next, identify potential threats using techniques like STRIDE (Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, and Elevation of Privilege). Then, assess the risks associated with each threat and prioritize them based on their potential impact.
Candidates should include steps such as identifying assets, understanding potential attackers' goals, and establishing appropriate security measures. A strong answer will reflect methodical thinking and comprehensive understanding of the process.
3. Can you give an example of a threat model you've worked on and what you learned from the process?
In a past project, I worked on a threat model for a financial app. We identified several potential threats, including unauthorized access attempts and data leakage. By addressing these threats early, we implemented robust access controls and encryption protocols.
An ideal candidate will not only recount the technical aspects but also reflect on the learning outcomes and how those experiences improved their subsequent threat modeling efforts.
4. How do you prioritize threats once they are identified in the threat modeling process?
Prioritizing threats involves assessing their potential impact and the likelihood of occurrence. Using a risk matrix can be helpful to visualize which threats require immediate attention based on their severity and probability.
Look for answers that demonstrate a balance between analytical skills and practicality. Candidates should be able to articulate a clear strategy for prioritizing and managing threats effectively.
5. What are some common challenges you face during threat modeling, and how do you overcome them?
Common challenges include incomplete information about the system, evolving threat landscapes, and balancing security with usability. To tackle these, I stay informed about the latest security trends and work closely with development teams to integrate security early in the design process.
Strong candidates will highlight their problem-solving skills and adaptability in overcoming such challenges. Their response should reflect proactive measures and continuous learning.
12 Software Security Engineer questions related to vulnerability assessments

To determine whether candidates can effectively identify and address security weaknesses in software systems, consider using these questions related to vulnerability assessments. These questions will help you evaluate a candidate’s proficiency in spotting potential threats and implementing robust security measures. For more insights on the Software Security Engineer role, explore our detailed job description.
- How would you conduct a vulnerability assessment for a new software project?
- Can you describe a tool you use for vulnerability scanning and why you prefer it?
- What steps do you take to classify and prioritize vulnerabilities once identified?
- How do you ensure that vulnerabilities are effectively communicated to the development team?
- What are the common challenges you face during a vulnerability assessment?
- How do you handle false positives during a vulnerability assessment?
- Can you provide an example of a critical vulnerability you discovered and how you addressed it?
- What role does automation play in your vulnerability assessment process?
- How do you integrate vulnerability assessments into the software development lifecycle?
- How do you approach a situation where a vulnerability needs to be addressed immediately in a live system?
- What are some best practices for remediating vulnerabilities in software applications?
- How do you measure the success of your vulnerability assessment processes?
14 situational Software Security Engineer interview questions for hiring top engineers

To identify top talent and ensure your candidates have the right skills for the role of a Software Security Engineer, consider asking these situational interview questions. They are designed to reveal how applicants think on their feet and apply their knowledge in real-world scenarios.
- How would you handle a situation where a critical security flaw is discovered just before a major software release deadline?
- Imagine you are working on a project with a tight budget. How would you ensure the software remains secure without overspending?
- A developer has introduced a new feature that is highly requested by users but poses potential security risks. How would you address this situation?
- Suppose a client reports a potential security vulnerability in your software. What steps would you take to assess and validate the claim?
- Describe a time when you encountered resistance to implementing a necessary security measure. How did you persuade others to accept it?
- How would you approach a scenario where a team is pressured to release a software update quickly, potentially compromising security testing?
- You discover a vulnerability in a software component that has already been widely deployed. What immediate actions would you take?
- If you had to explain a complex security issue to a non-technical audience, how would you ensure they understand the importance of addressing it?
- How would you balance the need for rapid deployment with the necessity of conducting thorough security assessments?
- Imagine you are tasked with integrating a new third-party service into your software. What security considerations would you prioritize?
- How would you manage a situation where an urgent patch needs to be applied across multiple systems, but not all teams are responsive?
- Suppose a security measure conflicts with a business requirement. How would you negotiate a solution that satisfies both security and business needs?
- How do you approach developing a security protocol for software that must comply with multiple regulatory standards?
- You detect unusual activity in a system outside normal working hours. What steps would you take to investigate and respond to this potential threat?
Which Software Security Engineer skills should you evaluate during the interview phase?
While it's impossible to assess every aspect of a candidate in a single interview, focusing on key Software Security Engineer skills can provide valuable insights. Here are the core competencies to evaluate during the interview process:
Secure Coding Practices
Secure coding practices are fundamental for Software Security Engineers. They need to understand how to write code that is resistant to common vulnerabilities and attacks.
To assess this skill, consider using an assessment test with relevant MCQs on secure coding principles and best practices.
You can also ask targeted interview questions to gauge their knowledge of secure coding. Here's an example:
Can you explain the concept of input validation and why it's important in secure coding?
Look for answers that demonstrate understanding of input validation as a security measure. Candidates should explain how it helps prevent attacks like SQL injection and cross-site scripting.
Threat Modeling
Threat modeling is a critical skill for identifying potential security risks in software systems. It helps engineers anticipate and mitigate vulnerabilities before they become issues.
To evaluate this skill, you might use an assessment that includes questions on threat modeling methodologies and risk assessment techniques.
During the interview, you can ask a question like this to assess their threat modeling skills:
How would you approach threat modeling for a new mobile banking application?
Listen for a structured approach that includes identifying assets, potential threats, and mitigation strategies. Candidates should mention considering various attack vectors and prioritizing risks.
Security Tools and Technologies
Software Security Engineers need to be proficient with various security tools and technologies. This includes familiarity with static and dynamic analysis tools, penetration testing frameworks, and security information and event management (SIEM) systems.
An assessment test focusing on common security tools can help evaluate a candidate's technical knowledge in this area.
To further assess their practical experience with security tools, you might ask:
What security testing tools have you used in your previous projects, and how did you apply them?
Look for answers that demonstrate hands-on experience with relevant tools. Candidates should be able to explain how they've used these tools to identify and address security vulnerabilities in real-world scenarios.
3 Tips for Using Software Security Engineer Interview Questions
Before you start putting what you've learned to use, here are our tips to make the most of your Software Security Engineer interviews.
1. Utilize Skill Tests Prior to Interviews
Skill tests help to filter out candidates who lack the necessary technical skills before they reach the interview stage. This saves time and ensures that only qualified candidates proceed further.
Consider using tests that align with the role's requirements. For software security engineers, you could use tests such as cyber security test, penetration testing test, or ethical hacking test.
Employing these tests as a preliminary step in your hiring process can improve the quality of candidates you interview. This allows you to focus on deeper assessments during the actual interview.
2. Compile a Concise List of Interview Questions
Time during interviews is limited, so it's important to select the right number and type of questions. This helps in evaluating candidates on various skills effectively.
Consider including questions that assess related skills to get a fuller picture of the candidate. For instance, questions on communication or problem-solving can reveal more about the candidate's abilities beyond technical expertise.
3. Ask Follow-Up Questions
Relying solely on preset questions may not provide a complete understanding of a candidate's capabilities. Follow-up questions are essential to gauge depth and authenticity.
For example, if a candidate discusses their experience with threat modeling, you could follow up with, 'Can you describe a specific challenge you faced during threat modeling and how you overcame it?' This can reveal the candidate's problem-solving skills and ability to apply their knowledge in real situations.
Use Software Security Engineer skills tests to hire talented professionals
If you're aiming to hire someone with software security skills, ensuring they possess the necessary expertise is key. The most effective way to verify this is by using skill tests. Consider using our Cyber Security Test or Penetration Testing Test to evaluate potential candidates.
Once you have the test results, you can shortlist the best applicants and invite them for interviews. To streamline your hiring process, visit our online assessment platform and make your recruitment more precise and efficient.
Cyber Security Assessment Test
Download Software Security Engineer interview questions template in multiple formats
Software Security Engineer Interview Questions FAQs
They should have knowledge in cryptography, network security, secure coding practices, and vulnerability assessment.
Ask them to describe their approach to identifying and mitigating potential threats in a given scenario.
Vulnerability assessments help identify and fix security weaknesses in a system before they can be exploited.
They provide insights into how candidates handle real-world security challenges and their problem-solving abilities.
This combination assesses both theoretical knowledge and practical application, ensuring a well-rounded evaluation.

40 min skill tests.
No trick questions.
Accurate shortlisting.
We make it easy for you to find the best candidates in your pipeline with a 40 min skills test.
Try for freeRelated posts
Free resources