Adaface Sample Kubernetes Questions
Here are some sample Kubernetes questions from our premium questions library (10273 non-googleable questions).
Skills
Aptitude & Soft Skills
Logical Reasoning
Abstract Reasoning
English
Reading Comprehension
Spatial Reasoning
Verbal Reasoning
Diagrammatic Reasoning
Critical Thinking
Data Interpretation
Situational Judgement
Attention to Detail
Numerical Reasoning
Aptitude
Quantitative Reasoning
Inductive Reasoning
Deductive Reasoning
Error Checking
English Speaking
Pronunciation
Product & Design
Visualization & BI Tools
Programming Languages
Frontend Development
Backend Development
Data Science & AI
Data Engineering & Databases
Cloud & DevOps
Testing & QA
Accounting & Finance
Microsoft & Power Platform
CRM & ERP Platforms
Cybersecurity & Networking
Marketing & Growth
Oracle Technologies
Other Tools & Technologies
| 🧐 Question | |||||
|---|---|---|---|---|---|
|
Medium
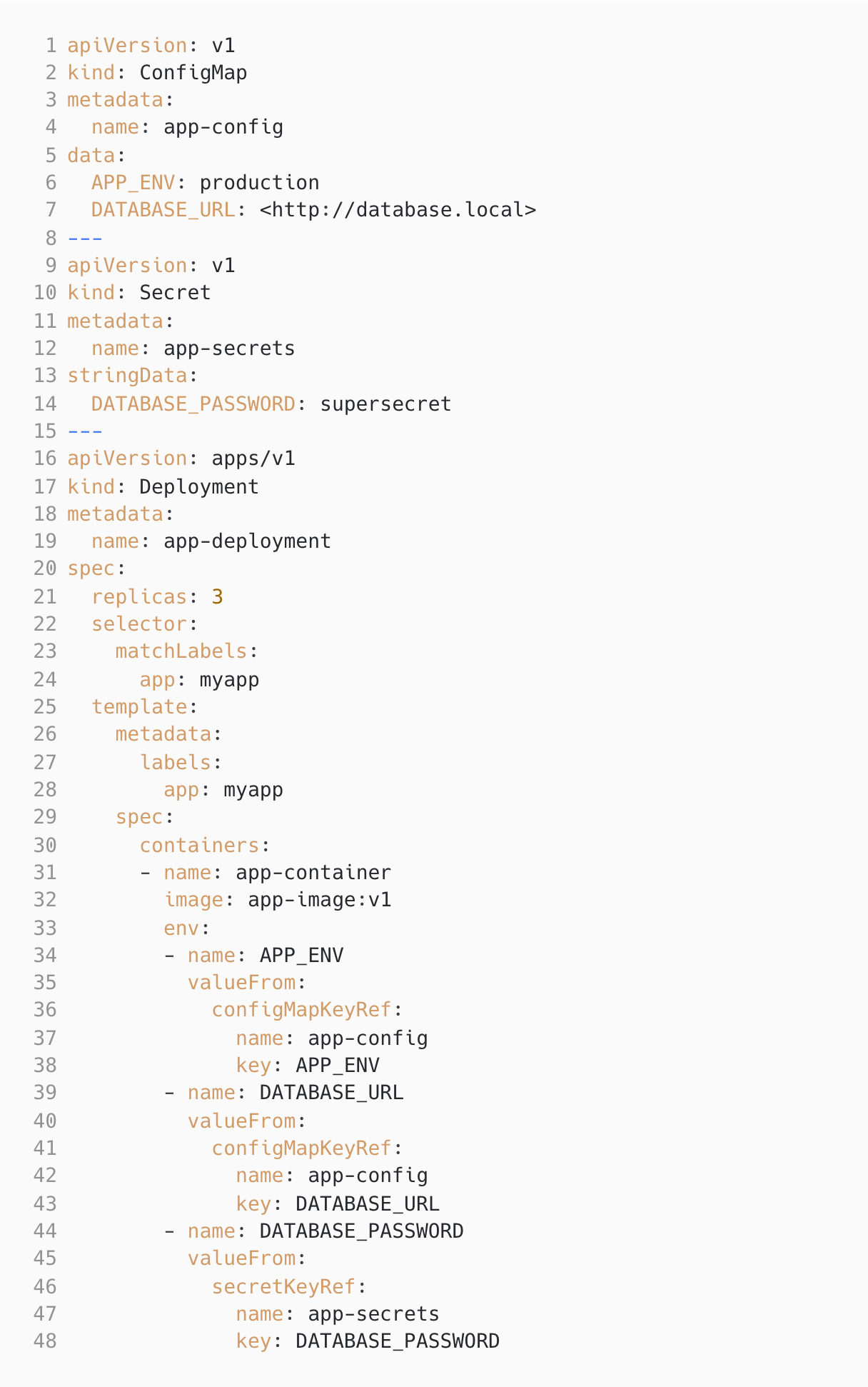
ConfigMap and Secrets Interaction
|
Solve
|
||||
|
|
|||||
|
Medium
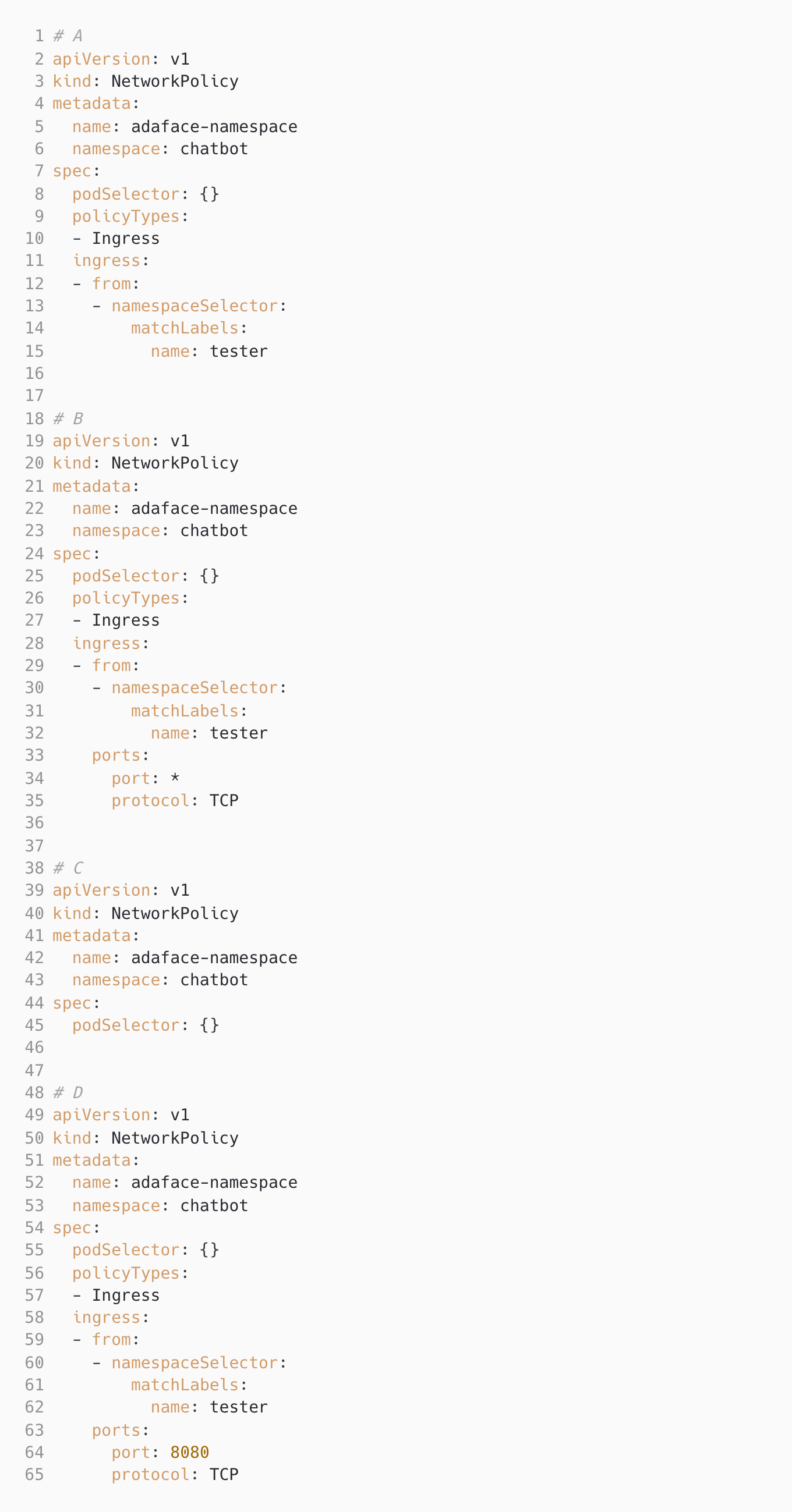
Ingress from namespace
|
Solve
|
||||
|
|
|||||
|
Medium
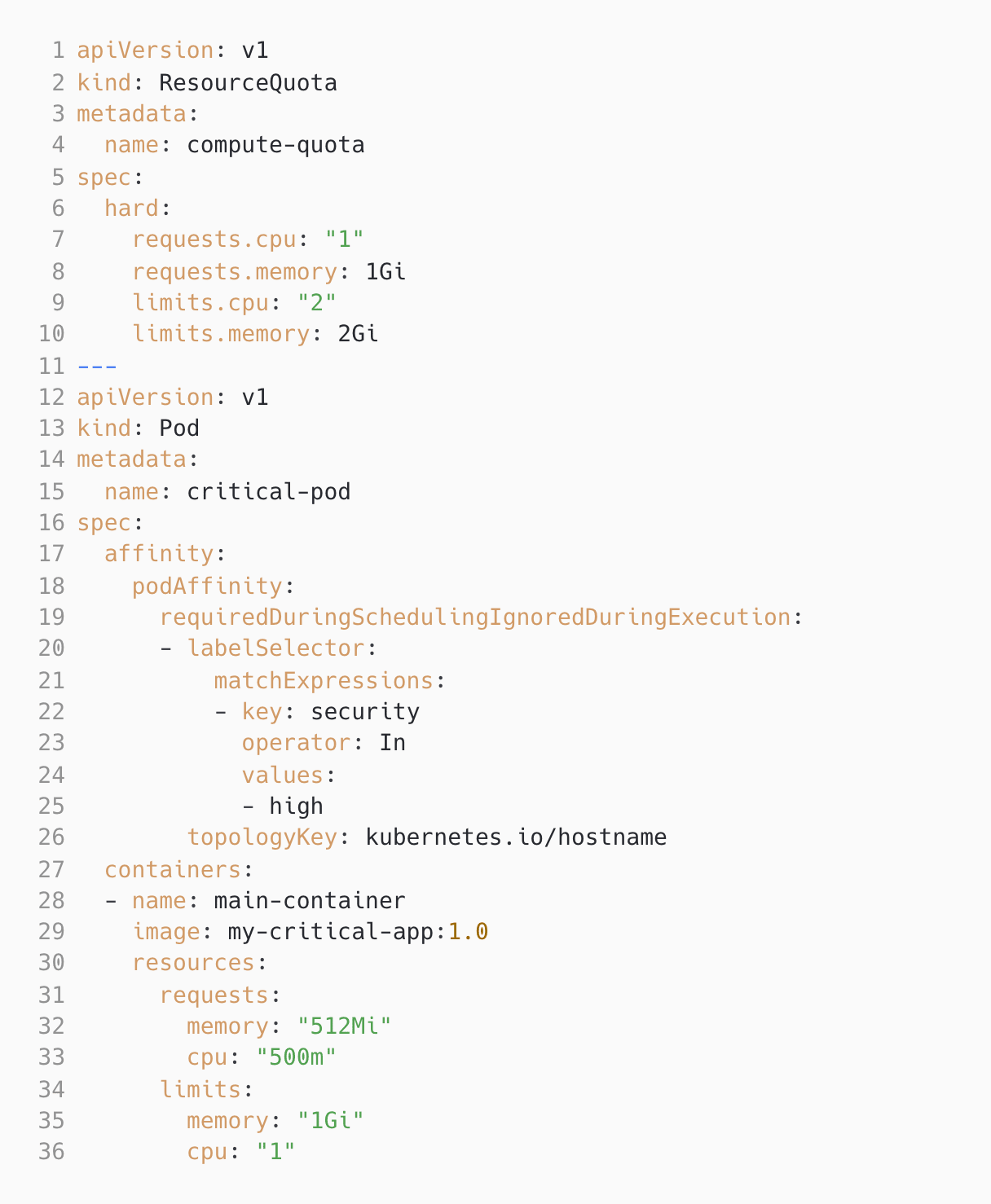
Pod Affinity and Resource Quota Compliance
|
Solve
|
||||
|
|
|||||
|
Easy
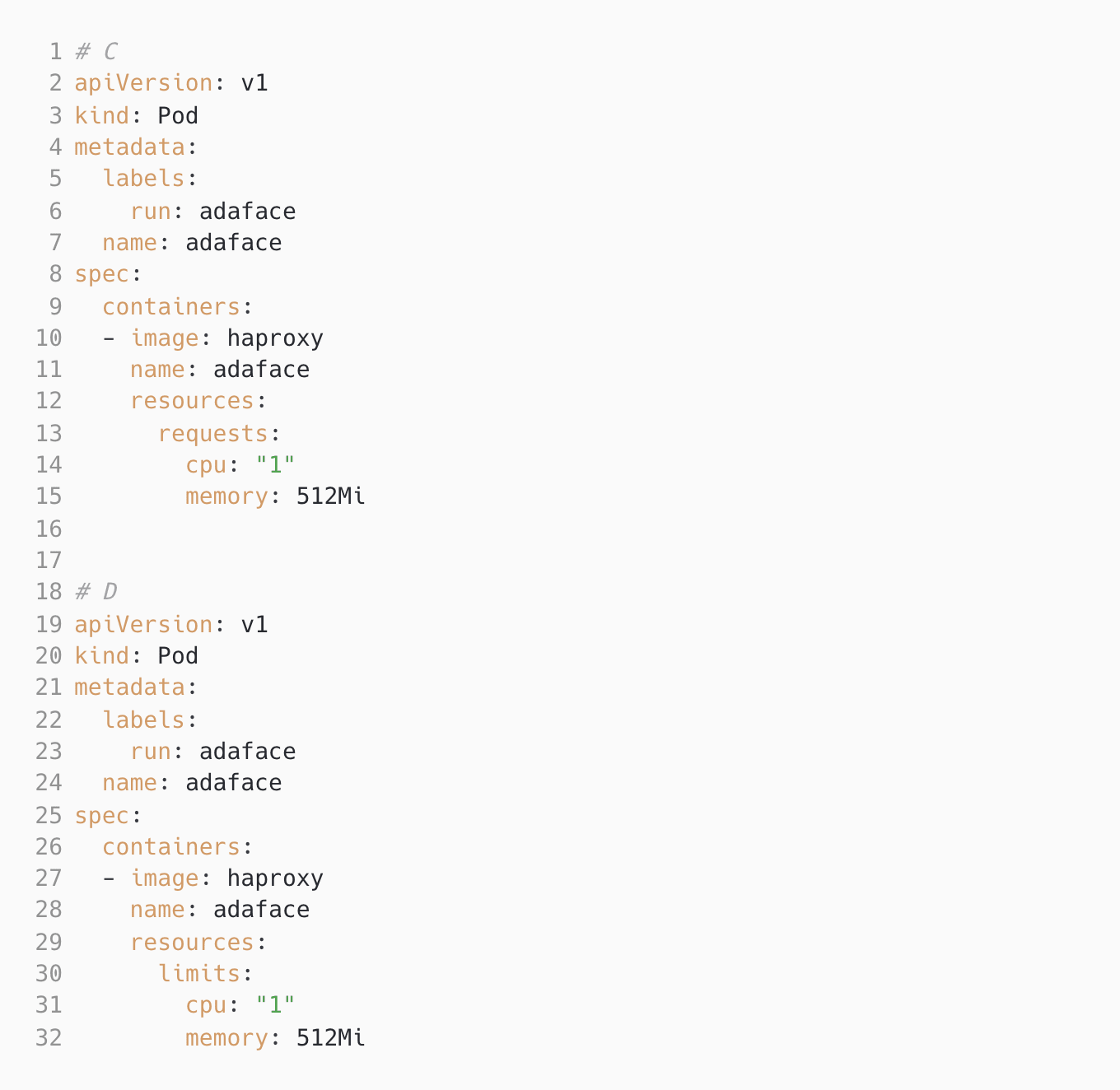
Resource limits
|
Solve
|
||||
|
|
|||||
| 🧐 Question | 🔧 Skill | ||
|---|---|---|---|
|
Medium
ConfigMap and Secrets Interaction
|
2 mins Kubernetes
|
Solve
|
|
|
Medium
Ingress from namespace
|
3 mins Kubernetes
|
Solve
|
|
|
Medium
Pod Affinity and Resource Quota Compliance
|
2 mins Kubernetes
|
Solve
|
|
|
Easy
Resource limits
|
3 mins Kubernetes
|
Solve
|
| 🧐 Question | 🔧 Skill | 💪 Difficulty | ⌛ Time | ||
|---|---|---|---|---|---|
|
ConfigMap and Secrets Interaction
|
Kubernetes
|
Medium | 2 mins |
Solve
|
|
|
Ingress from namespace
|
Kubernetes
|
Medium | 3 mins |
Solve
|
|
|
Pod Affinity and Resource Quota Compliance
|
Kubernetes
|
Medium | 2 mins |
Solve
|
|
|
Resource limits
|
Kubernetes
|
Easy | 3 mins |
Solve
|

We evaluated several of their competitors and found Adaface to be the most compelling. Great library of questions that are designed to test for fit rather than memorization of algorithms.
Swayam Narain, CTO, Affable



Join 1200+ companies in 80+ countries.
Try the most candidate friendly skills assessment tool today.

Ready to streamline your recruitment efforts with Adaface?
Ready to streamline your recruitment efforts with Adaface?