Navigating the world of networking roles can be challenging, especially when it comes to identifying the right candidates for your team. From junior network engineers to senior network architects, understanding the right questions to ask can save you time and ensure a quality hire.
This blog post is a comprehensive guide featuring various networking interview questions tailored to different expertise levels, from basic to advanced. It also includes specialized questions on protocols, services, and network security to assess specific skills.
By incorporating these questions into your interviews, you can more effectively evaluate candidates' competencies and experience. For a more thorough pre-interview assessment, consider using our network engineer test.
Table of contents
15 basic Networking interview questions and answers to assess applicants

To determine whether your applicants have the right skills and knowledge for roles like network engineer, ask them some of these 15 basic networking interview questions. These questions are designed to help you assess their foundational understanding of networking concepts and practices.
- Can you explain what an IP address is and why it is important?
- What is the difference between a router, a switch, and a hub?
- How does a VPN work and why is it used?
- What is a subnet and why is subnetting used?
- Can you describe the OSI model and its layers?
- What is the difference between TCP and UDP?
- Explain what DNS is and how it functions.
- What is NAT and how does it work?
- How would you secure a network?
- What are the common network protocols you are familiar with?
- Can you explain what a MAC address is and its significance?
- How do you troubleshoot a network connectivity issue?
- What is a firewall and how does it enhance network security?
- What is DHCP and why is it used in networking?
- Describe the difference between IPv4 and IPv6.
10 Networking interview questions and answers to evaluate junior network engineers

Interviewing junior network engineers can be challenging, especially when you need to assess a wide range of skills and knowledge. This list of questions will help you evaluate candidates effectively by focusing on key areas of networking fundamentals and problem-solving abilities. Use these questions during the technical interview to gauge the candidate's practical understanding and readiness for the role.
1. Can you explain what a network topology is and why it is important?
A network topology refers to the layout or organizational hierarchy of interconnected nodes of a computer network. It outlines how different network devices and components are connected and communicate with each other.
Understanding network topology is crucial as it impacts the network's performance, scalability, and fault tolerance. Different topologies like star, ring, and mesh have their own advantages and limitations.
An ideal candidate should explain the significance of choosing the correct topology based on the specific needs of the organization, such as minimizing latency or maximizing redundancy.
2. What steps would you take to diagnose a network slowdown?
To diagnose a network slowdown, I would start by identifying whether the issue is isolated to specific devices or widespread across the network. Checking for hardware issues, such as malfunctioning routers or switches, would be the next step.
I would then analyze network traffic to identify any unusual spikes or bottlenecks. Tools like network analyzers can be helpful in pinpointing the source of the problem. Finally, I'd review logs and configurations for any recent changes that might have caused the slowdown.
Look for candidates who can outline a clear, methodical approach and who are familiar with common diagnostic tools. This shows their practical experience in handling network issues.
3. How do you prioritize tasks when multiple network issues occur simultaneously?
Prioritizing tasks in the face of multiple network issues involves evaluating the impact of each issue on business operations. Critical systems or services should be addressed first, especially those affecting a large number of users or essential business functions.
Communication with stakeholders is also vital to understanding priorities and managing expectations. Regularly reassessing the situation and adjusting priorities as necessary ensures the most critical problems are resolved first.
Candidates should demonstrate their ability to perform impact analysis and maintain clear communication with team members and stakeholders. Look for examples of how they have successfully managed multiple issues in past roles.
4. What is the role of a network administrator in ensuring network security?
A network administrator is responsible for implementing and maintaining security measures to protect the network from unauthorized access, attacks, and data breaches. This includes configuring firewalls, setting up secure access protocols, and monitoring network traffic for suspicious activity.
Regularly updating software and hardware, applying security patches, and conducting security audits are also key responsibilities. The administrator must stay current with the latest security threats and best practices to keep the network secure.
Ideal candidates should emphasize their proactive approach to network security and their experience with various security tools and protocols. They should also highlight the importance of continuous monitoring and regular updates.
5. Can you explain what load balancing is and why it is used?
Load balancing is the process of distributing network or application traffic across multiple servers to ensure no single server becomes overwhelmed. It helps in optimizing resource use, maximizing throughput, and minimizing response time.
By balancing the load, it also provides redundancy, which enhances the network's reliability and availability. If one server fails, the load balancer redirects traffic to other functioning servers, ensuring continuous service.
Candidates should explain the importance of load balancing in maintaining performance and reliability, and provide examples of when they have implemented or worked with load balancing solutions.
6. Describe a time when you had to implement a network upgrade. What steps did you take?
When implementing a network upgrade, planning is critical. I began by assessing the current network infrastructure and identifying the areas that needed improvement. I also gathered requirements from stakeholders to understand their needs.
Next, I created a detailed upgrade plan, including a timeline, resources needed, and potential risks. I tested the upgrade in a controlled environment before rolling it out to the entire network. Finally, I monitored the network closely post-upgrade to ensure everything was functioning as expected.
The best answers will demonstrate a structured approach to planning and execution, as well as the candidate's ability to anticipate and mitigate risks. Look for specific examples and any lessons learned from the experience.
7. How do you stay current with the latest networking technologies and trends?
Staying current with the latest networking technologies and trends is crucial for a network engineer. I regularly read industry blogs, follow key influencers on social media, and participate in online forums and communities.
Attending webinars, conferences, and taking part in professional development courses also helps me stay updated. Additionally, I experiment with new technologies in lab environments to understand their practical applications.
Ideal candidates should show a proactive approach to continuous learning and professional development. They should provide examples of specific resources they use and how they apply new knowledge to their work.
8. What would you do if you discovered a security vulnerability in the network?
If I discovered a security vulnerability, my first step would be to assess the severity and potential impact of the vulnerability. I would then document my findings and report them to the relevant stakeholders.
Immediate action would involve applying patches or updates to mitigate the risk. If a patch is not available, I would implement temporary measures, such as restricting access or disabling affected services, until a permanent solution is found.
Candidates should demonstrate their ability to act quickly and responsibly. Look for answers that emphasize thorough documentation, communication, and a well-structured approach to mitigating security risks.
9. How do you ensure effective communication with non-technical stakeholders?
Effective communication with non-technical stakeholders involves using clear, jargon-free language and focusing on the business impact rather than technical details. I make an effort to understand their perspective and concerns.
Visual aids like diagrams and charts can help convey complex information more easily. Regular updates and open channels of communication also ensure that stakeholders are informed and engaged throughout the process.
Assess whether candidates can simplify complex technical concepts and relate them to business objectives. Look for examples of successful communication with non-technical stakeholders in their past experiences.
10. Can you explain the concept of network redundancy and its importance?
Network redundancy involves creating multiple pathways for data to travel within a network, ensuring that if one pathway fails, another can take over without any disruption in service. This is critical for maintaining network reliability and uptime.
Redundancy can be achieved through methods such as using backup devices, multiple connections, and failover protocols. It minimizes the risk of a single point of failure affecting the entire network.
Candidates should highlight the importance of redundancy in disaster recovery and business continuity. Look for their understanding of different redundancy methods and their experience in implementing them.
18 intermediate Networking interview questions and answers to ask mid-tier network engineers

To assess the technical proficiency of mid-tier network engineers, use these 18 intermediate networking interview questions. These questions are designed to evaluate a candidate's deeper understanding of networking concepts and their ability to handle more complex scenarios.
- Explain the difference between a collision domain and a broadcast domain.
- How does OSPF (Open Shortest Path First) routing protocol work?
- What is a VLAN and how does it improve network performance?
- Describe the process of ARP (Address Resolution Protocol) and its importance.
- What is QoS (Quality of Service) and how is it implemented in a network?
- Explain the concept of VRF (Virtual Routing and Forwarding) and its use cases.
- How does BGP (Border Gateway Protocol) differ from interior gateway protocols?
- What is a MPLS (Multiprotocol Label Switching) network and its advantages?
- Describe the differences between unicast, multicast, and broadcast traffic.
- How does Network Address Translation (NAT) affect the OSI model?
- What is a DMZ (Demilitarized Zone) and why is it used in network security?
- Explain the concept of VXLAN (Virtual Extensible LAN) and its benefits.
- How does STP (Spanning Tree Protocol) prevent network loops?
- What is the difference between a Layer 2 and Layer 3 switch?
- Describe the process of troubleshooting a VPN connection issue.
- How does SNMP (Simple Network Management Protocol) work for network monitoring?
- Explain the concept of network segmentation and its importance in security.
- What are VLANs trunking protocols and how do they function?
6 advanced Networking interview questions and answers to evaluate senior network architects

When interviewing senior network architects, you need questions that dig deep into their expertise and problem-solving abilities. These advanced networking questions will help you evaluate candidates' knowledge of complex network designs, emerging technologies, and strategic thinking. Use them to identify top talent who can lead your organization's networking initiatives and tackle challenging infrastructure projects.
1. How would you design a network architecture for a multi-cloud environment?
A strong answer should outline a comprehensive approach to designing a multi-cloud network architecture. Key points to cover include:
- Implementing a robust network security strategy, including firewalls, VPNs, and encryption
- Utilizing software-defined networking (SDN) for flexibility and scalability
- Ensuring consistent policies and governance across all cloud environments
- Implementing cloud-native networking services for optimal performance
- Designing for high availability and disaster recovery
- Considering hybrid cloud connectivity options like dedicated lines or cloud exchanges
Look for candidates who demonstrate a deep understanding of cloud networking concepts and can articulate the challenges and solutions specific to multi-cloud environments. Follow up by asking about their experience with specific cloud platforms or tools they've used for multi-cloud management.
2. Explain the concept of Intent-Based Networking (IBN) and its potential impact on network management.
Intent-Based Networking (IBN) is an approach to network management that uses AI and machine learning to automate planning, design, and management of networks. It allows network administrators to define high-level business intentions, which the system then translates into network configurations.
Key aspects of IBN include:
- Automated translation of business intent into network policies
- Continuous monitoring and verification of network state
- Automated remediation of network issues
- AI-driven predictive analysis and optimization
Look for candidates who can explain how IBN differs from traditional network management approaches and its potential benefits, such as reduced complexity, improved agility, and enhanced security. Strong answers might also discuss challenges in implementing IBN and its relationship to software-defined networking (SDN).
3. How would you approach designing a zero-trust network architecture?
A zero-trust network architecture is based on the principle of 'never trust, always verify.' It assumes that threats can exist both outside and inside the network perimeter. Key elements of a zero-trust design include:
- Micro-segmentation of network resources
- Strong authentication and authorization for all users and devices
- Continuous monitoring and logging of all network activity
- Least privilege access control
- Encryption of data in transit and at rest
- Regular security assessments and updates
Evaluate candidates based on their understanding of zero-trust principles and their ability to explain how these concepts can be practically implemented. Look for answers that emphasize the importance of identity verification, context-aware access policies, and continuous monitoring in maintaining a secure network environment.
4. Describe how you would implement network automation in a large enterprise environment.
Implementing network automation in a large enterprise requires a strategic approach. A comprehensive answer should cover:
- Assessing current network infrastructure and identifying automation opportunities
- Choosing appropriate automation tools and platforms (e.g., Ansible, Puppet, Python scripts)
- Developing a phased implementation plan
- Creating standardized templates for network configurations
- Implementing version control for network configurations
- Integrating with existing systems (IPAM, CMDB, etc.)
- Establishing automated testing and validation procedures
- Training network administrators and engineers on new automation tools and processes
Look for candidates who can articulate the benefits of network automation, such as reduced human error, faster deployment times, and improved consistency. They should also be aware of potential challenges, like initial setup complexity and the need for cultural changes within the IT team.
5. How would you design a network to support IoT devices at scale?
Designing a network for IoT devices at scale requires careful consideration of several factors:
- Scalability: Using technologies like IPv6 to support a large number of devices
- Security: Implementing device authentication, encryption, and network segmentation
- Connectivity: Choosing appropriate wireless technologies (e.g., Wi-Fi, cellular, LoRaWAN)
- Data management: Implementing edge computing and data aggregation strategies
- Power efficiency: Optimizing network protocols for low-power devices
- Interoperability: Ensuring compatibility between different IoT devices and protocols
- Monitoring and management: Implementing robust systems for device and network monitoring
Evaluate candidates based on their understanding of IoT-specific networking challenges and their ability to propose solutions that balance performance, security, and scalability. Look for answers that demonstrate awareness of emerging IoT standards and protocols.
6. Explain the concept of Network Function Virtualization (NFV) and its implications for network design.
Network Function Virtualization (NFV) is a network architecture concept that uses virtualization technologies to manage core networking functions via software rather than hardware. Key aspects include:
- Decoupling network functions from proprietary hardware appliances
- Running network functions as software on standard servers
- Enabling dynamic scaling and management of network services
- Reducing hardware costs and power consumption
- Improving agility in deploying new network services
Look for candidates who can explain how NFV differs from traditional networking approaches and its potential benefits, such as reduced CAPEX and OPEX, increased flexibility, and faster service deployment. Strong answers might also discuss challenges in implementing NFV, such as performance concerns and the need for robust orchestration and management systems.
12 Networking interview questions about protocols and services

To evaluate candidates' knowledge of essential networking protocols and services, use this list of targeted questions. These inquiries can help you gauge the applicant's technical expertise and problem-solving abilities, crucial for roles like a network engineer.
- What is the purpose of the ICMP protocol and how is it used in network troubleshooting?
- Can you explain the handshake process in TCP and its significance?
- What is the role of a proxy server in network architecture?
- How does the HTTPS protocol secure data transmission over the internet?
- What are the functions of the Kerberos protocol in network security?
- Explain the differences between the different types of load balancers.
- What is the purpose of the RADIUS protocol in network access control?
- How does IPsec enhance network security and what are its key components?
- Can you describe the differences between FTP and SFTP?
- What is the role of the Syslog protocol in network management?
- How does the SNTP protocol differ from NTP and when would you use it?
- Can you explain the concept of anycast and its advantages in DNS?
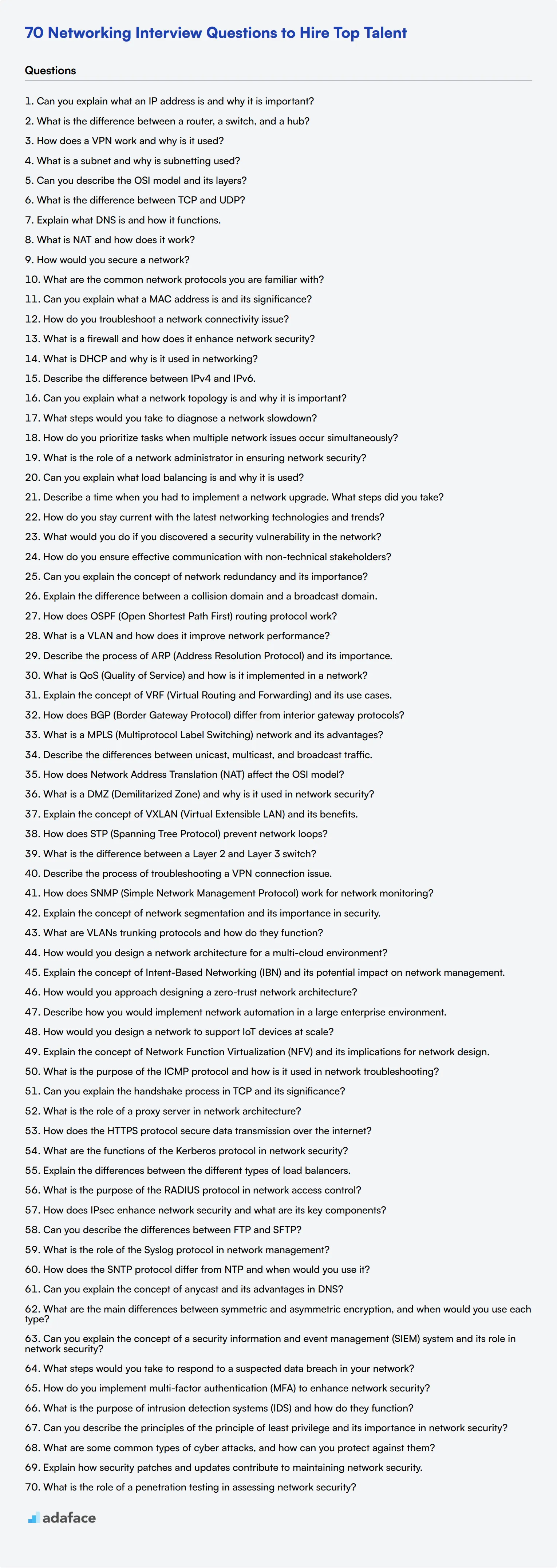
9 Networking interview questions about network security
To ensure your candidates have a solid grasp of network security concepts, consider using this list of interview questions. These targeted questions can help you assess their understanding and practical skills in crucial areas of network protection. For more detailed insight, check out a sample network engineer job description.
- What are the main differences between symmetric and asymmetric encryption, and when would you use each type?
- Can you explain the concept of a security information and event management (SIEM) system and its role in network security?
- What steps would you take to respond to a suspected data breach in your network?
- How do you implement multi-factor authentication (MFA) to enhance network security?
- What is the purpose of intrusion detection systems (IDS) and how do they function?
- Can you describe the principles of the principle of least privilege and its importance in network security?
- What are some common types of cyber attacks, and how can you protect against them?
- Explain how security patches and updates contribute to maintaining network security.
- What is the role of a penetration testing in assessing network security?
Which Networking skills should you evaluate during the interview phase?
While a single interview might not reveal everything about a candidate's capabilities, focusing on core networking skills can provide crucial insights. These skills are instrumental in determining a candidate's ability to perform networking tasks effectively.
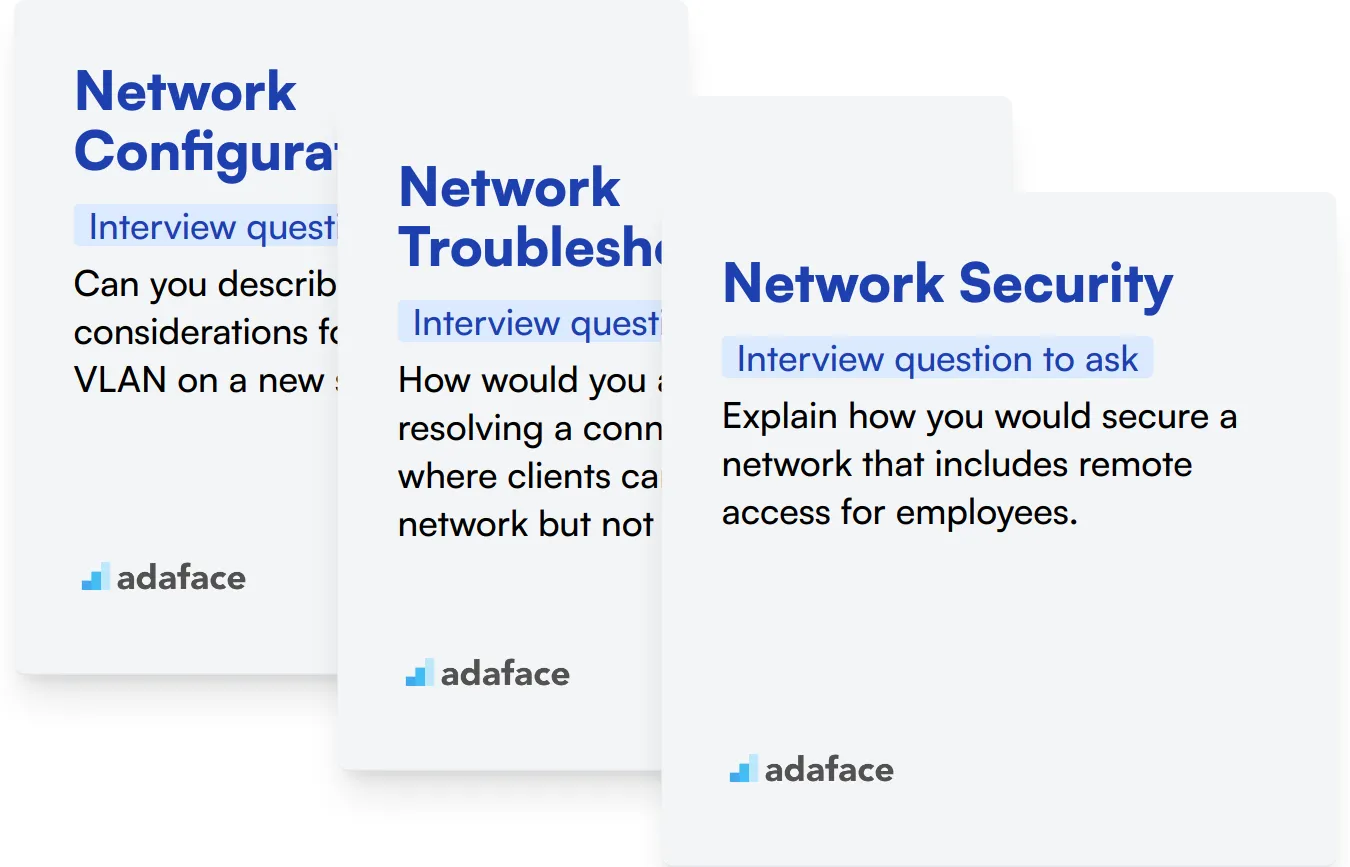
Network Configuration
The ability to configure networks is fundamental for any networking role, as it involves setting up and maintaining the operational status of network devices. A strong grasp of network configuration ensures smooth and secure communication within and between networks.
To assess a candidate's knowledge in network configuration, consider utilizing a multi-choice question assessment. Adaface's network engineer test can help identify candidates with the necessary skills.
During the interview, you can directly gauge a candidate's practical understanding by asking specific questions about network configuration.
Can you describe the process and considerations for configuring a VLAN on a new switch?
Look for detailed knowledge in their response, such as awareness of VLAN tagging and trunking concepts, alongside specific command line configurations they might use.
Network Troubleshooting
Troubleshooting is a critical skill in networking, necessary for diagnosing and resolving network issues quickly. This capability ensures minimal downtime and optimal network performance.
An effective way to pre-assess this skill is through scenarios-based MCQs, which can simulate common networking problems.
Further test their troubleshooting skills by posing practical network scenarios during the interview.
How would you approach resolving a connectivity issue where clients can connect to the network but not the internet?
Evaluate their methodical approach to diagnosing issues, looking for structured problem-solving techniques like checking IP configurations, DNS settings, and examining router/gateway settings.
Network Security
Network security is vital to protect data integrity and prevent unauthorized access. Knowledge in this area is essential to safeguard company assets and maintain trust.
You can use targeted MCQs to initially filter candidates based on their understanding of security protocols and defense strategies. Adaface's cyber security test will help streamline this process.
To delve deep into their expertise, consider asking relevant questions about the latest security measures and protocols in networking.
Explain how you would secure a network that includes remote access for employees.
Critical points in their response should include multifactor authentication, secure VPN configurations, and regular audits of access logs and security protocols.
Enhance Your Team by Hiring the Best Networking Professionals with Adaface
When searching for top talent with networking skills, it's important to verify that candidates possess the necessary expertise and knowledge effectively.
The most reliable way to assess these skills is through targeted skill tests. Consider utilizing the Network Engineer Test or the Cisco Routing & Switching Online Test from Adaface to gauge the technical competencies accurately.
After administering these tests, you can filter and identify the highest-performing candidates, ensuring that only the most qualified individuals are advanced to the interview stage.
To streamline your recruitment process, start by signing up at our Dashboard or explore more about our offerings on the Online Assessment Platform page.
CISCO Routing Switching Test
Download Networking interview questions template in multiple formats
Networking Interview Questions FAQs
Look for clear, concise answers that demonstrate practical knowledge and problem-solving skills.
You can tailor the questions based on your company’s specific networking tools, technologies, and scenarios.
Be cautious of vague responses, lack of practical examples, and an inability to explain basic concepts clearly.
Expect more technical detail from senior candidates and practical knowledge from junior candidates.
Start with basic questions to warm up the candidate, then move to more complex scenarios and problem-solving questions.

40 min skill tests.
No trick questions.
Accurate shortlisting.
We make it easy for you to find the best candidates in your pipeline with a 40 min skills test.
Try for freeRelated posts
Free resources